Introduction
Azure Functions app provides Authorization Level (Anonymous/Function/Admin) options during Function App creation in your code. It is more on Authorization of your App or API but if you want to bring authentication to your function app, we have App Service Authentication feature.
App Service Authentication by default is Off on Azure Function App and users will not be promoted for Login. App service authentication provides below authentication providers
- Azure Active Directory
- Microsoft Account
- Facebook
- Google
- Twitter
Where to Find App Service Authentication in Portal
Open your Function App > Left menu > Settings > Configuration > Authentication / Authorization.
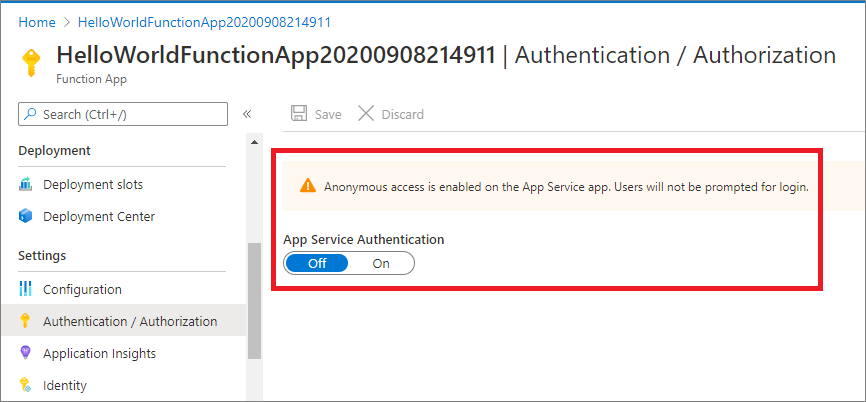
Fig 1 : Function App with App Service Authentication is Off by default
Create Function App
Refer step by step guide(http://www.dotnetmirror.com/articles/microsoft-azure/226/create-azure-function-app-using-visual-studio-step-by-step-guide) to create your first function app and deploy to Azure. Below screenshot shows we are able to access the function app without any Authentication in front of it.
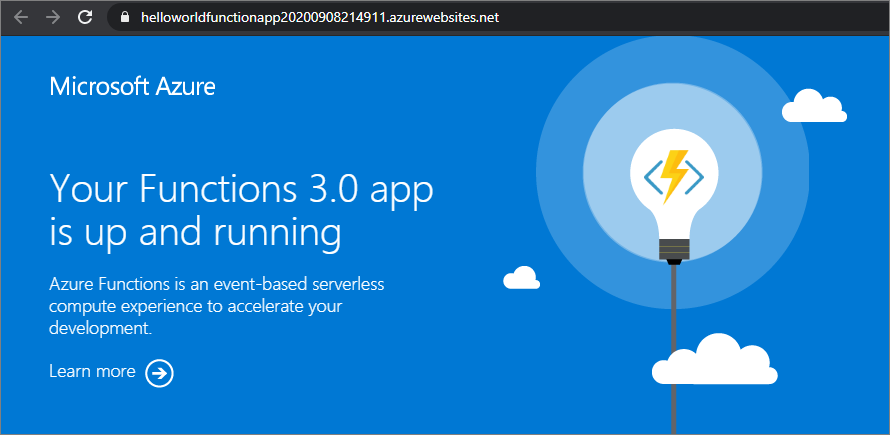
Fig 2 : Function App with Authentication
In this post, let us look at how to Authenticate Azure function apps using Azure Active Directory(AAD) as an authentication provider.
Configure Azure Active Directory
- From the Authentication/Authorization left menu, Select On from App Service Authentication and you can see authentication providers like Azure AD, Microsoft, Facebook, Google and Twitter.
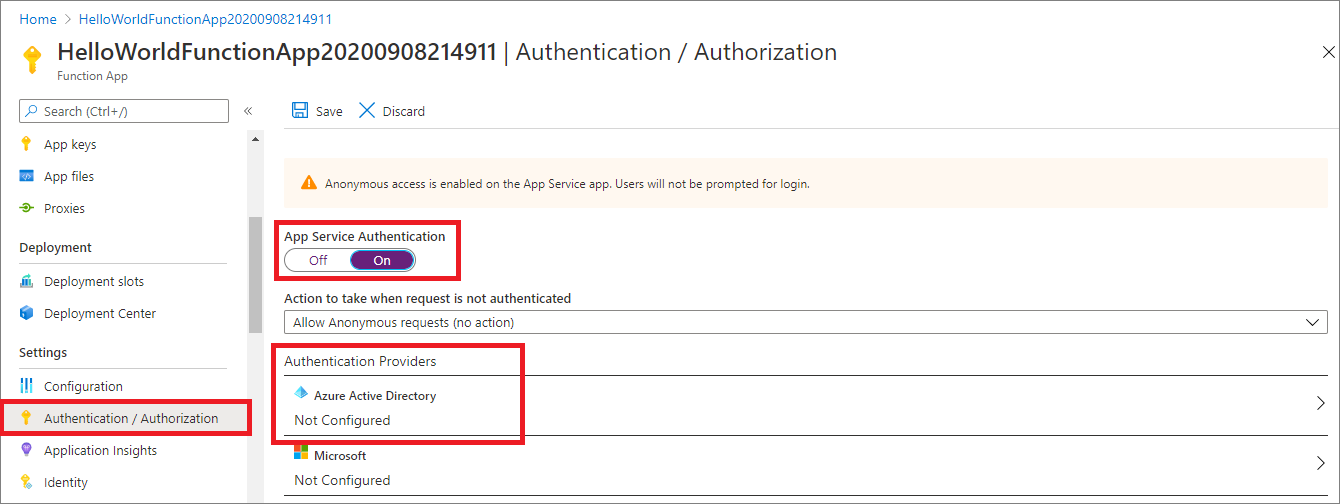
Fig 3 : Select Azure Active Directory Authentication Provider
- Select “Azure Active Directory” from Authentication Providers. It opens the Azure Active Directory setting page.
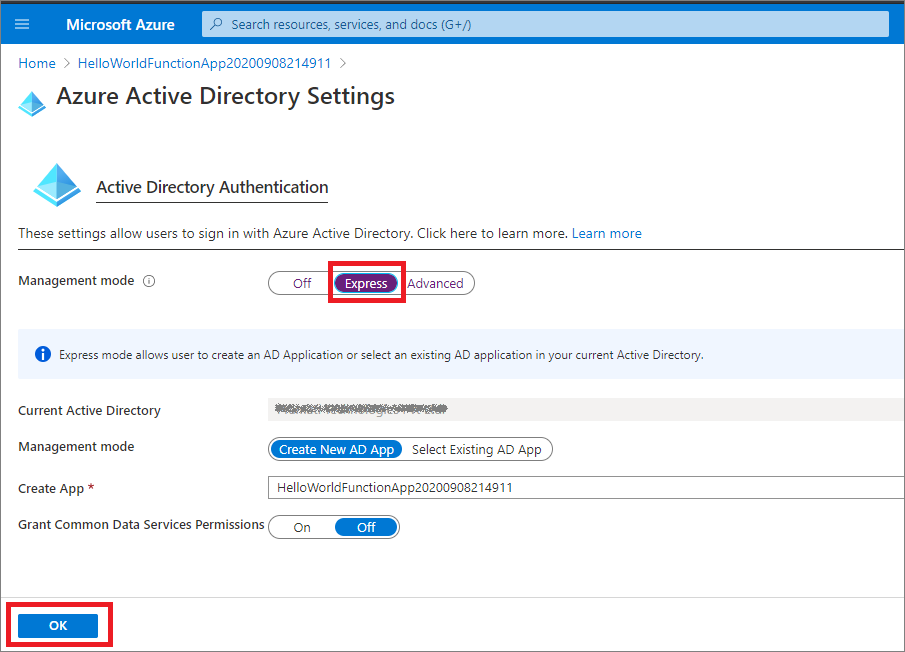
Fig 4 : Azure Active Directory Settings
- Select “Express” from Management mode. (Note: From advanced tab, you can also add Client ID, Tenant ID, APP ID URI and Secret directly if you have existing app in AAD).
- It selects your Current Active Directory and we have options to create New AD App or Select Existing AD App
- Select Create New AD App and it comes with a dynamic App Name which registers the app to your Active Directory. (Note: If you Select Existing AD App, you can select existing apps which are already registered under “App registration” from Azure Active Directory)
- Click on OK.
- It takes back to “App Service Authentication” page
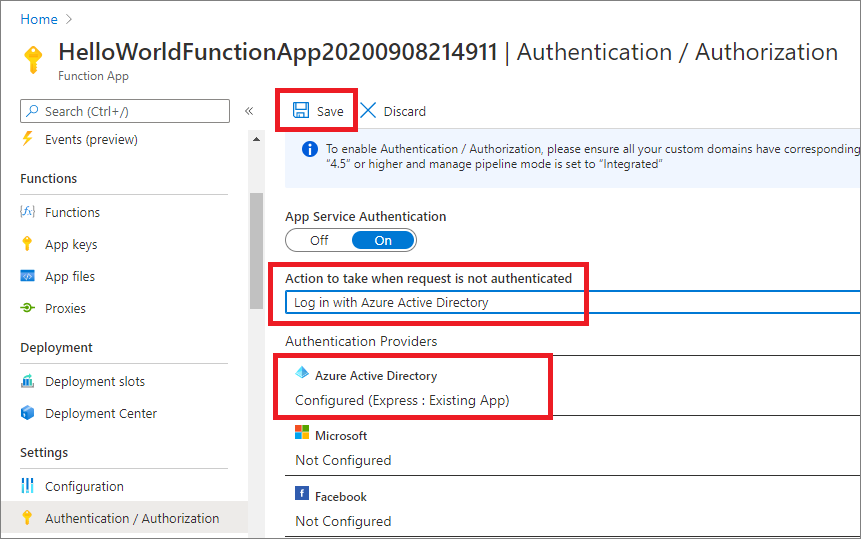
Fig 5 : Login with Azure Active Directory Settings
- Select “Log in with Azure Active Directory” from “Action to take when request is not authenticated”
- Click on Save
Now if you try to access the App, it asks you login with your Azure AD.
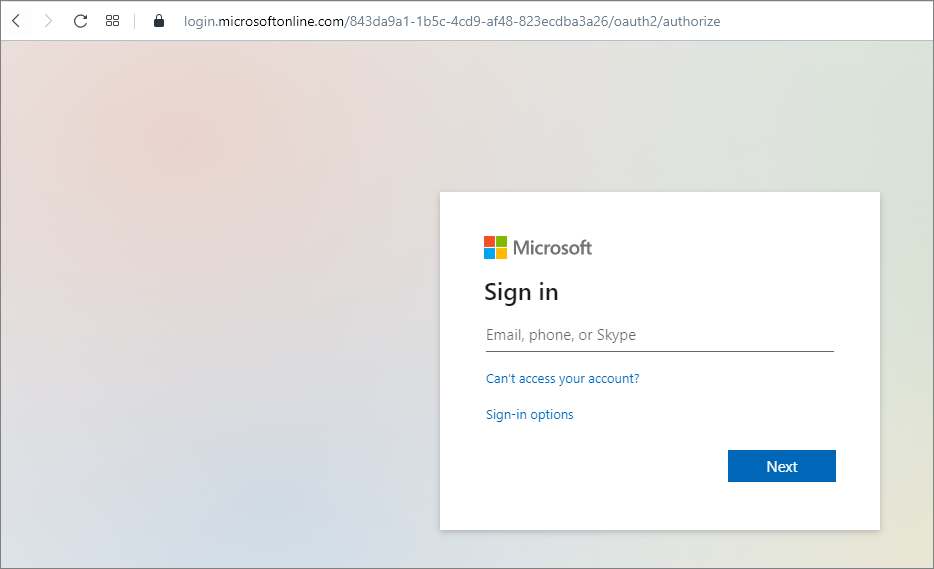
Fig 6 : Function App prompts AAD login
Login with your Azure AD from your organization (within AAD tenant). Once you are a valid user, it asks for your Permissions to access the app.
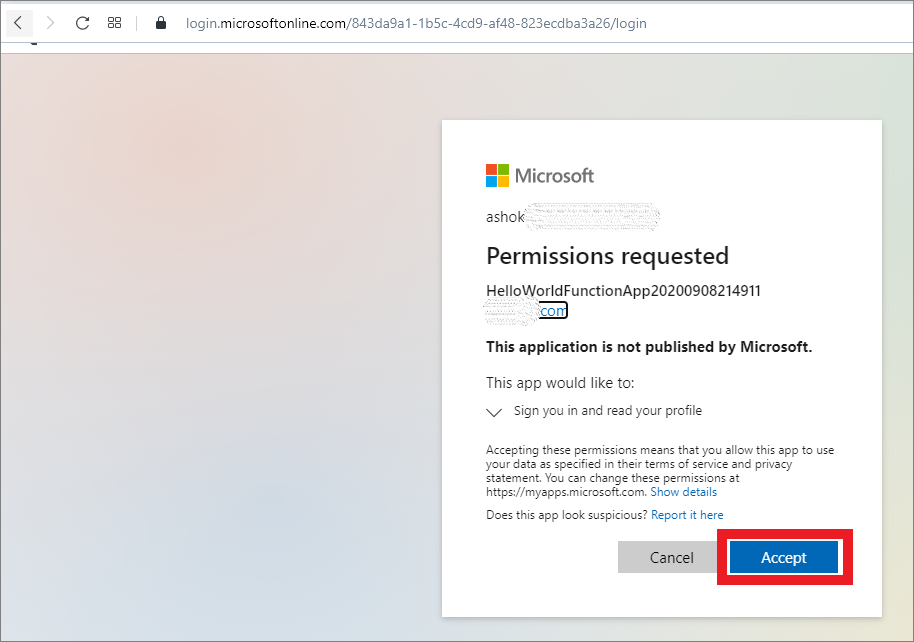
Fig 7: Function App prompts AAD permissions
Once you Accept it and your account is within your organization tenant AD, you should be able to access the Function App.
Note: This process is more on Authentication, still you need to implement Authorization on your app code.
Let's Look how the App is registered.
We selected “Create New AD App” during configurations. In the background it created and registered a new app in Azure Active directory. From Azure portal, open Azure Active Directory > App registrations > Registered app must be available where Application ID URI shows your Function App URL.
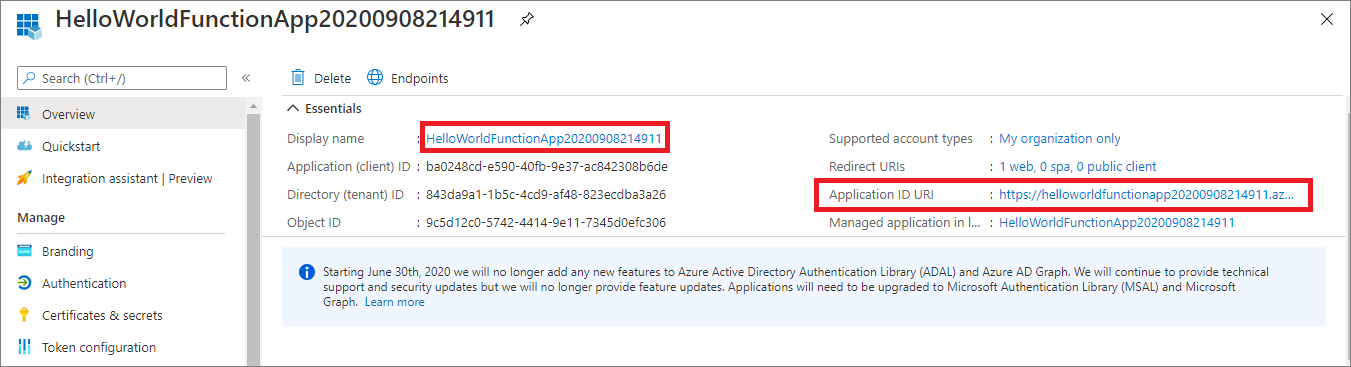
Fig 8: Registered a new App in AAD with your Function URL as Application ID URL
Who can access the App
From the registered app, select Authentication tab from the left menu and you can see by default “Account in this Organization directory only(your organizing name[xxxxxx] -single tenant) can access the application.
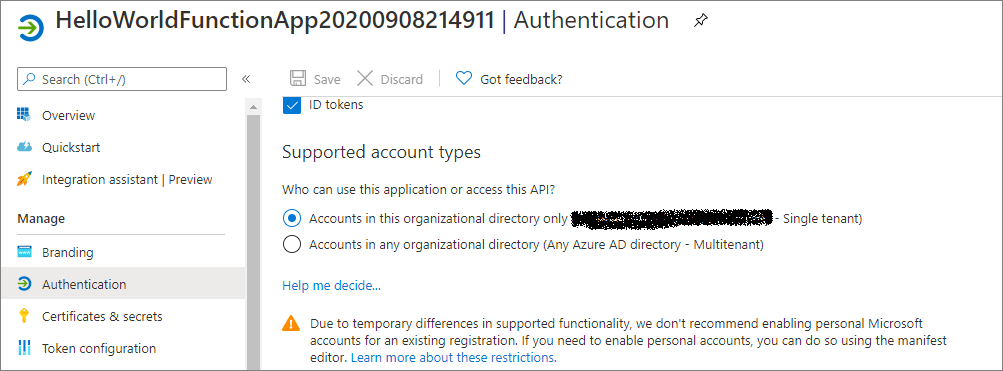
Fig 9 : Registered app - Authentication users
Let's try to access the App with personal account(out of tenant)
If you try to access the app with your personal account(out of your organization tenant account), you will get below error.
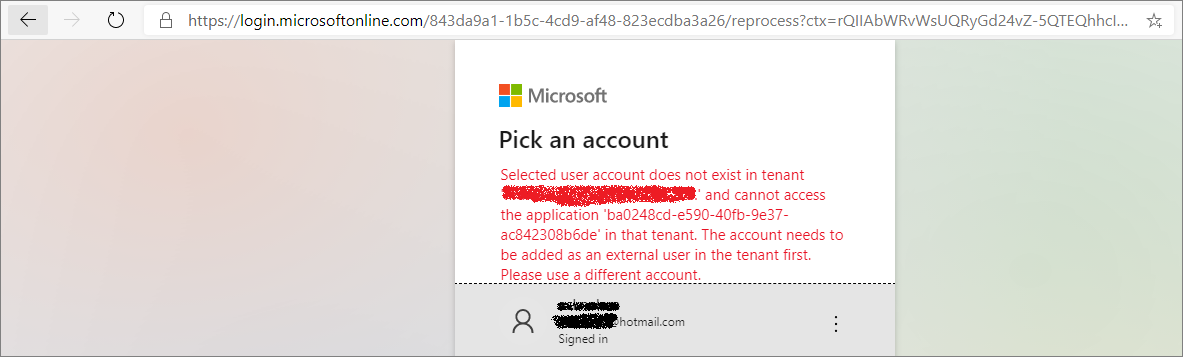
Fig 10 : Access App with personal account(out of tenant)
Note: This AAD authentication provider feature is not available in Linux consumption for Azure functions.
How to disable Authentication
If you want disable authentication, select Off from App Service Authentication. Click on Save.
Conclusion
We learnt how to configure Azure Active directory authentication provider on Azure function and added authentication to your app for additional security.
References